
Crypto ransomware and how to restore your files
Have you been subject to file lock-down by a form of ransomware?
You are not the only one!
As an I.T Administrator I have recently dealt with a high volume of encrypted files that had been locked by Crypto – Ransomware. In the past things such as Cryptolocker and other forms malware had locked files down for in return a sum of money from the individual or group that had infected the PC/Network. Probably the easiest way to get rid of this is to pay the attacker. Though you do not want to do this if possible, because funding the trade will only make matters worse in the long run, the more money people get by doing this criminal act the more common you will find the same problem occurring.
Recently major advertisement networks have been affected who provide adverts to big name sites such as BBC, MSN, AOL and The New York Times, just to name a few. The criminals have had ad-space on these networks that then go onto the websites you visit. These ad-spaces have malicious code in that will exploit holes in your browser and any software running inside of it. Which means the unknowing user can get infected without noticing a single thing has changed. These do not only come through via the web, but also through things such as email, p2p/ file sharing, anyway your computer or network has access to an outside source. To read more on the exploits use google and to find out about the recent exploits such as the Angler Exploit.
I read a case where a hospital had been infected with a Crypto type ransomware in February this year (2016). They had to pay out $17,000 just to gain access to their files, meanwhile their patients were being redirected to another hospital. Now this is a serious matter! What would happen if these attackers actually encrypted files that held personal information about patient’s needs, or maybe measurements of medication they require? This could be fatal, ransomware is putting people’s lives at risk indirectly.
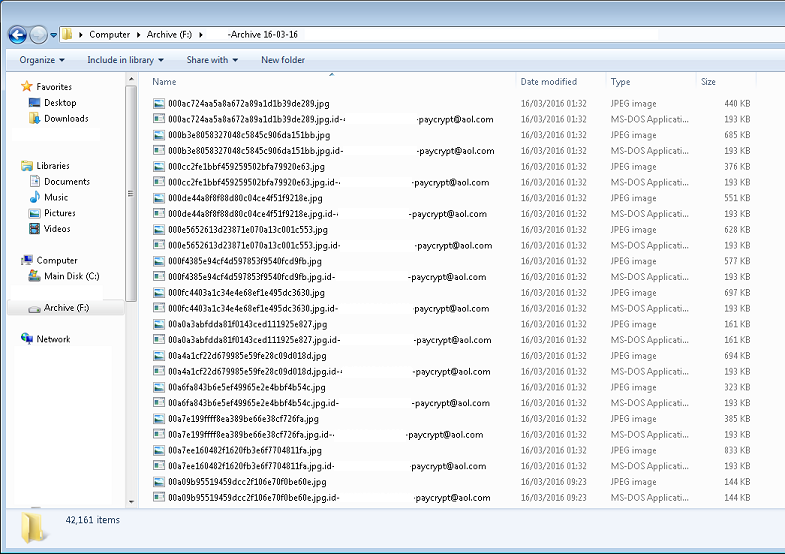
The most recent variant that I have come across was “paycrypt” [email protected] was the address left by the attacker. The files are encrypted with a key that the victim does not have. The same scenario with any ransomware, the attacker will ask for money to get access to your files. [email protected] (I strongly advise against dealing with the attackers) had searched through all networked files and tried to encrypt and lock them, computers that have ‘open’ file directories will be affected on the network
Ways to Restore Your Files
If you are infected with a newer variant you will not be able to decrypt your files, though if you are infected with crypt0l0cker prior 2012 actually 2 groups in the past actually wrote an application to decrypt your files called decryptolocker. You may be able to find it on bleepingcomputer.com. There are also tools such as Tesla Decryption Tool, to decrypt TeslaCrypt another form of crypto ransomware.
So for the people that have files encrypted but do not want to pay the ransom. The only thing you can do is restore from backups.
Newer versions of Windows have an active backup shadow copy of files. If this is turned on- on your system, you are in luck.
To do this right click a folder that has been affected and the click properties-> then go to the tab previous version. On that tab you will be able to restore previous versions of files that windows has kept a shadow copy of.
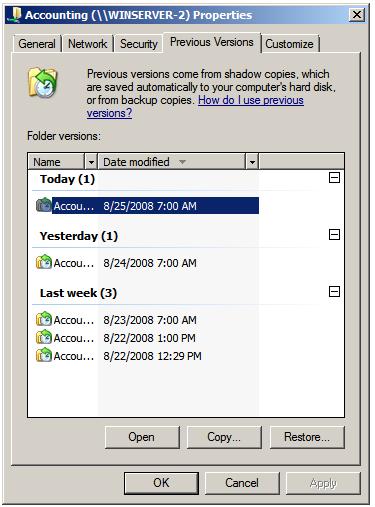
If you manage to restore data this way and you can verify that the normalized files are restored, you can go ahead and delete the files that hold the encrypted data.
There are other tools that can help you recover files, here is a list from a google search I have used Recuva by Priform and it works great to recover deleted files. The problem with using these tools to help towards recovering from these type of attacks is that usually they look for a deleted version of the file. Whereas encryption changes the file, and doesn’t leave a copy or other data behind it.
You should be keeping backups of any documents you have, not once but twice, this brings us on to prevention.
Preventing These Attacks
If you are the owner of a large or small network, you should have a filter or firewall in place. This protects your data and your users from malicious attacks. These do not always have to cost a fortune, but not being protected could cost you your business, your memories or someone’s life (see above).
I recommend Untangle, this piece of software sits on a machine between your internet gateway (usually your router) and the PC’s on your network. You may have multiple gateways or 1000’s of PCs on your network, these can all run through Untangle. You can use Untangle on the “lite” version for free though of course I’d recommend upgrading. It may seem a bit extreme for small networks but I’d recommend implementing it for as little as a 5 device network.
Other than a firewall you must keep your anti-virus up to date, make sure on each PC and if you do not have a network version of an anti-virus I would recommend it. Being able to run scans and update virus definitions from a central location is more than handy, it’s a saviour. I’d recommend AVG.
No anti-virus that I know of can protect us fully, fundamentally an anti-virus can only protect you against what it knows how to protect you against. Other threats such that use zero-day exploits and attacks, are much harder to stop. Zero-day is literal, and meaning as soon as an exploit is found it is used against a victim. Anti-virus are unable to detect zero-day attacks as they do not have any knowledge of them yet! There are some measures that anti-virus, anti-malware, anti-root kit and anti-spyware software can take, like guessing if an object/file is a threat to your system, or checking if it detects suspicious activities on the system. Though it is neither impenetrable and can sometimes classify legit files operations into the wrong category.
Further Disaster Recovery
Backups -backups backups backups, not a prevention but to recover from a disaster you need more than one form of backup in place.
 Whether you are an individual backing up to an external HDD or a large business backing up to a NAS or Cloud online storage option you must take multiple backups, or snapshots at different dates.
Whether you are an individual backing up to an external HDD or a large business backing up to a NAS or Cloud online storage option you must take multiple backups, or snapshots at different dates.
I know some that some users think that backing up a few files to a pen drive is enough, this is NOT the case. Pen drives, usb sticks, memory cards can easily get corrupted, not to mention lost. Many NAS drives are available and I’d recommend investing into one. Before choosing how you backup things you should read up what the best solution is for your situation. Keeping on topic of Crypto ransomware, what would have happened if your backups were incremental and as soon as the file was encrypted your backup solution noticed the changed and push the now encrypted file onto your backup storage. You would then have 2 files your direct copy and your backup also encrypted. The problem with this is you would not have a clean backup of the file.
Some cloud based solutions such as dropbox, offer previous versions of files so you can restore files to a certain date, I believe this is a 30 day period and then on they have a feature called extended file history. With an onsite solution such as external hard drives and NAS drives you want to have a feature that will take “snapshot” backups to ensure that when hit by an attack such as crypto ransomware you can restore to another date.
I hope by outlining these issues, and giving insight to ransom-ware, this information can help you protect your own system.